Planning and Controlling Risk Responses
It is important that planned responses are appropriate to the significance of the risk, cost effective in meeting the challenge, realistic within the project context, agreed upon by all parties involved, and owned by a responsible person. The individual owner of each risk will need to communicate with the appropriate stakeholders who may be impacted by it's occurrence as part of managing the risk.
 |
The risk plan defines the level of risk which is seen as acceptable, how risks will be managed, who will be responsible for carrying out risk related activities, the time and cost of each risk activity and how the communication of risk is to occur. You will need to use this along with the risk register to plan your responses. See the risk register template.
 |
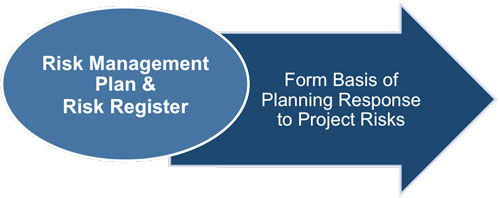
There are four possible strategies for dealing with threats or risks that may have negative impacts on the project.
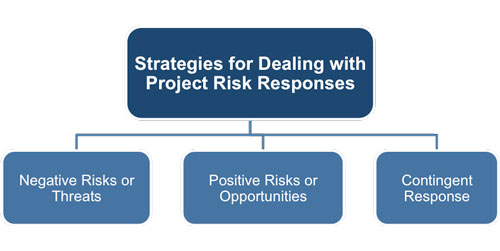
1. Avoid - This involves taking action to either reduce the probability of the risk and/or its impact to zero. In either case this response enables the risk to be circumvented entirely. For example, using a certain supplier might carry the risk of them going out of business during the course of the project. This risk could be avoided by using a supplier who was bigger, better established and more financially secure.
2. Transfer - This involves transferring the risk to a third party so that they are responsible for its management and impact. It does not eliminate the risk it simply transfers the liability to someone else. This can be done by:
o Taking out insurance (the insurance company is now liable) or
o Having the work done under a fixed-price contract (the contractor is now liable).
Risk transference nearly always involves payment of a risk premium to the party taking on the risk and may introduce new risks. For example, an insurance company may contest the claim or a contractor might dispute the terms and conditions of the contract if they are having problems delivering.
 |
3. Mitigate - Taking early action to reduce the probability and/or impact of a risk occurring is often more effective than trying to repair the damage after it has occurred. Adopting less complex processes, conducting more tests, or choosing a more stable supplier are examples of mitigation actions.
4. Accept - The most common acceptance strategy is to establish a contingency reserve, including amounts of time, money, or resources to handle the risks. It is usually chosen either because: the risk is low in terms of impact or probability, or the cost and effort of taking a different action is out of proportion to the risk itself.
There are four possible strategies for dealing with opportunities.
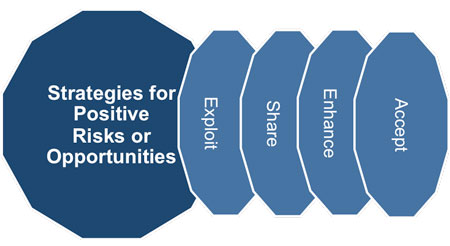 |
1. Exploit - examples of directly exploiting responses include assigning an organization's most talented resources to the project to reduce the time to completion or to provide lower cost than originally planned.
2. Share - sharing a positive risk involves allocating some or all of the ownership of the opportunity to a third party who is best able to capture the opportunity for the benefit of the project. Examples of sharing actions include forming risk-sharing: Partnerships, Teams, Special-purpose companies, or Joint ventures (JVs).
These can be established with the express purpose of taking advantage of the opportunity so that all parties gain from their actions.
3. Enhance - examples of enhancing opportunities include adding more resources to an activity to finish early.
4. Accept - accepting an opportunity is being willing to take advantage of it if it comes along, but not actively pursuing it.
This is the process of implementing risk response plans, tracking identified risks, monitoring residual risks, identifying new risks, and evaluating risk process effectiveness throughout the project.
Planned risk responses that are included in the project plan are executed during the life cycle of the project, but the project work should be continuously monitored for new, changing, and outdated risks. There are several techniques that can be used to control risks
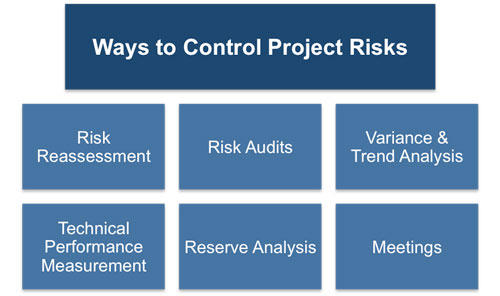 |
Reassessment
Project risk reassessments should be regularly scheduled to keep the risk register updated. The amount and detail of repetition that is appropriate depends on how the project progresses relative to its objectives, as well as, which risks (if any) actually manifest themselves.
Audits
These should be scheduled in the risk plan and examine the effectiveness of risk responses in dealing with identified risks and their root causes. The objectives should be clearly defined in advance and the audit may form part of the routine project review meetings, or may be run separately, each producing its own project audit report.
Trend Analysis
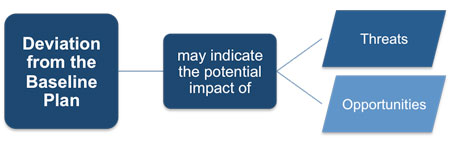
Earned value analysis and other methods of project variance and trend analysis may be used for monitoring overall project performance. Outcomes from these analysis may forecast potential deviation of the project at completion from cost and schedule targets. Deviation from the baseline plan may indicate the potential impact of threats or opportunities.
 |
Performance Measurement
This is designed to indicate the degree of technical risk faced by the project. Where deliverables can be measured against the plans in a quantitative way e.g.: Response times, Number of defects, etc. This can predict the degree of success in achieving the technical aims of the project.
Reserve Analysis
This compares the contingency reserves remaining to the amount of risk remaining at any time in the project in order to determine if the remaining reserve is adequate.
Implementing contingency plans or workarounds sometimes results in a change request.
• Recommended preventive actions are documented directions to perform on activity that can reduce the probability of negative consequences associated with project risks.
• Recommended corrective actions include contingency plans and workarounds.
The latter are responses that were not initially planned, but are required to deal with emerging risks that were previously unidentified or accepted passively.
If the approved change requests have an effect on the process of managing risk, the corresponding component documents of the project plan are revised and reissued to reflect the approved changes.
You may also be interested in:
Project Risk Management | Creating a Risk Management Plan | Identifying Project Risks | Performing a Risk Analysis | Planning and Controlling Risk Responses.
|
|